[Note. This is a slightly modified version of an article that originally appeared in issue 265 of Acorn User (November 2003).]
Until the late 20th century, strong cryptography was the preserve of government agencies and the military. But thanks to the advent of fast modern computers, cryptography with a 'military' level of security is now available to the masses.
Cryptography is so commonplace nowadays that many people are even unaware that they are using it in their everyday business. If you have ever used a PIN to obtain cash from a bank's ATM, or a secure webpage to order goods over the internet with a credit card number, you have used cryptography.
In order to discuss this subject, it is useful to define some conventional terminology.
The word 'cryptography' originates from the Greek: kruptos (hidden) + graphein (to write). Cryptography is the science of creating secure cryptosystems for making data unintelligible to those for whom it is not intended.
Cryptography is complemented by cryptanalysis, the science of 'attacking' cryptosystems, i.e. cracking them or discovering weaknesses in them. Together, these form cryptology. Modern cryptography has become strong only because of the interaction of these two branches of cryptology. As cryptanalysis reveals weaknesses in various cryptosystems, cryptographers devise new and stronger cryptosystems in order to defeat all known methods of cryptanalysis.
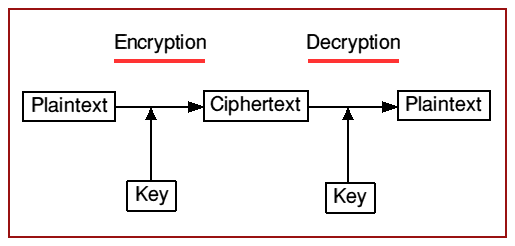
The following figure illustrates the general scheme of a cryptosystem:

The original data is known as the plaintext, and it is encrypted to produce the ciphertext. The reverse process, decryption, reproduces the original plaintext. The methods of encryption and decryption in any particular cryptosystem are described by a fixed set of mathematical rules, known as an algorithm, but the precise way in which the data is transformed in each of these two operations depends on a key.
An important principle of modern cryptography is that the algorithms used in any cryptosystem should be publicly known. Only then is it possible for experts to analyse the system and verify its resistance to all known cryptanalytic attacks, so that users may have confidence in it. In other words, the security of any encrypted data should rely solely on the secrecy of the decryption key, and not on any hidden encryption or decryption algorithms.
In the cryptographic community, dubious encryption software is commonly called 'snake oil', a term which originated from quack medicine peddled by travelling salesmen. Snake oil includes software for which the source code is not made publicly available, or for which the cryptographic algorithms have not been rigorously tested and analysed by expert cryptanalysts.
Those who know little about serious cryptography often assume that a particular encryption method is safe if nobody has cracked it. Cryptographers do not see it that way. As the eminent cryptographer Bruce Schneier put it, "That's actually backwards. In the world of cryptography, we assume something is broken until we have evidence to the contrary." In other words, a cryptosystem must be subjected to serious analysis by experts before it can be trusted.
In modern cryptography the plaintext is represented in a computer file, which is basically a sequence of bits, each having the value 0 or 1. One often speaks of the plaintext as a 'message', but in reality it may be any data that can be represented in a computer, such as an image or sound file.
A cipher is an algorithm for converting one sequence of bits into another of equal length, where the result depends on a key. In a symmetric cipher, the most common type, the same key is used for encryption and decryption. In other words, if a symmetric cipher is applied twice in succession, the original message is recovered.
The details of how modern ciphers work are rather technical mathematically and need not concern us here, but the general scheme of operation of a symmetric cipher is easy to understand from the following figure:
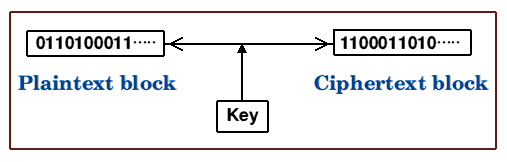
In general, the key for a cipher is simply a large number. Key lengths are conventionally measured in bits, and most of the well known strong ciphers have key lengths between 128 and 256 bits (powers of 2 being most common). A cipher is considered 'strong' if extensive analysis by the world's best cryptographers reveals that it is resistant to all known cryptanalytic attacks. In particular, there should be no known attack more efficient than 'brute force', i.e. testing all possible keys to find the one that decrypts a given message.
When brute force is the best known cracking method, it is easy to estimate the strength of a cipher by calculating the time needed to test all possible keys, using existing technology. Consider, for example, a cipher that uses 128-bit keys. This allows a colossal number of possible keys. Suppose, for example, that 10 billion computers are assigned to the task of cracking a particular encrypted message, each capable of testing 10 billion keys per second. Then, if you have a little mathematical ability, you can verify that it would take about 100 billion years to test all possible keys. That's longer than the estimated age of the universe according to modern cosmology, which is about 15 billion years. This is typical of the strength of modern ciphers.
To be fair, on average it would be necessary to run through only half of the keys to find the correct one. But you will probably agree that this is pretty good security!
With each additional bit of a key, the time required to test all keys is doubled. Therefore, even if computers become unimaginably faster in the future, the same degree of security could easily be maintained by moving to larger keys.
Of course, since the security of a message encrypted with a symmetric cipher relies on the secret key that was used to encrypt it, it is of paramount importance to keep that key absolutely secure.
Messages sent over the internet usually pass through several relaying hosts before reaching their destination. Such messages are analogous to messages sent on a postcard through the postal system - they can be read by anyone with access to any of the computers through which they pass.
Privacy can be ensured by using encryption. But symmetric ciphers are inadequate for secure communication over the internet. If two people who cannot meet in person want to communicate securely, how can they exchange a secret key? If they have a secure channel for doing this, they may as well exchange the message itself!
Public-key cryptography offers a neat solution to this conundrum. In a public-key cryptosystem, each user has a pair of keys: a public key and a secret key. On the basis of some rather clever mathematics, these two keys are constructed in such a way that each reverses the action of the other, but nevertheless there is no known feasible way for anyone to calculate one from a knowledge of the other.
The public key can be publicised widely, in the same way that most people publicise their telephone numbers. In fact, there are 'key servers' on the internet, so that anyone who knows the name and e-mail address of a particular user can look up that user's public key. A message can be encrypted for a particular user by encrypting it with that user's public key. Only that user can decrypt it, because nobody else has access to the corresponding secret key.
A public key is sometimes compared to a padlock. If a public key is like a padlock, then the matching secret key is like the ordinary key that opens the padlock.
This analogy goes even further if the padlock is regarded as the analogue of not only the public key, but also the cryptosystem. There may be only a few popular types of padlock, but each allows millions of possible cuts of keys. There is no loss of security in allowing anyone to see the brand of padlock that is used (or the cryptosystem plus the public key). The security rests entirely on the secrecy of the particular key that opens the padlock (or the secret key in a public-key cryptosystem).
The scheme shown in Figure 1 is again applicable to public-key cryptography, except that the two keys are different in this case. A public key is used for encryption, and the corresponding secret key for decryption. Just as in the case of symmetric ciphers, these keys consist of large numbers. In practice, the keys are stored in computer files, not remembered by the user. Since the secret key must be protected against unauthorised use, it is stored only in encrypted form, using a symmetric cipher, and the user can 'unlock' it by means of a passphrase whenever the software requires it.
Modern public-key cryptography offers the same degree of security as for symmetric ciphers, as discussed above, provided sufficiently large keys are used. But for technical reasons, public-key cryptography requires larger keys, typically 1024 to 2048 bits, to ensure a similar degree of security.
In this article I have discussed only the general concepts of modern cryptography. The reader will be glad to know that the methods discussed above can be implemented by means of user-friendly software in modern computers, including RISC OS computers. 'Military-grade' security is available to everyone.
In future articles I shall describe the RISC OS software that can be used for strong cryptography, including PGP and GnuPG. Meanwhile, readers may like to look at the available programs collected on my website at http://www.queen.clara.net/pgp/acorn.html.
Further information about modern cryptography can be found in another article with the same title, which I originally wrote for Archive magazine.